- Adobe1
- Akeneo1
- Alcatel-Lucent Enterprise9
- Amazon Business5
- Auth06
- Awin1
- AWS8
- CloudFlare6
- Commvault2
- Commvault-Infoniqa2
- Confluent7
- Diligent16
- Easyvista2
- Elastic7
- Esker6
- Fastly4
- Forcepoint2
- Forrester2
- Fortinet16
- Genesys18
- Genesys and Frontline Solutions3
- Genesys and TechneValue3
- Hornetsecurity5
- infoblox1
- Informatica2
- Izertis1
- Juniper1
- Kaspersky2
- Knowmad Mood3
- Kofax1
- LastPass4
- Lookout26
- Mobica4
- NFON2
- NordPass2
- NTT DATA1
- Nutanix10
- Okta13
- OneTrust2
- OpenText3
- Outpost244
- Performance One1
- PrestaShop Checkout2
- Qlik1
- Quantum2
- Quest2
- Recorded Future3
- Red Hat9
- Rubrik2
- Salesforce21
- SAP1
- ServiceNow9
- SoftwareOne4
- Specops Software1
- Sprinklr4
- Stormshield6
- Talkdesk8
- Tenable4
- Thales3
- Trend Micro4
- Tungsten Automation1
- Veeam27
- Verint2
- WALLIX5
- WALLIX & Reti S.p.A.1
- Weber2
- Wind River10
- Zoom31
- Zscaler12
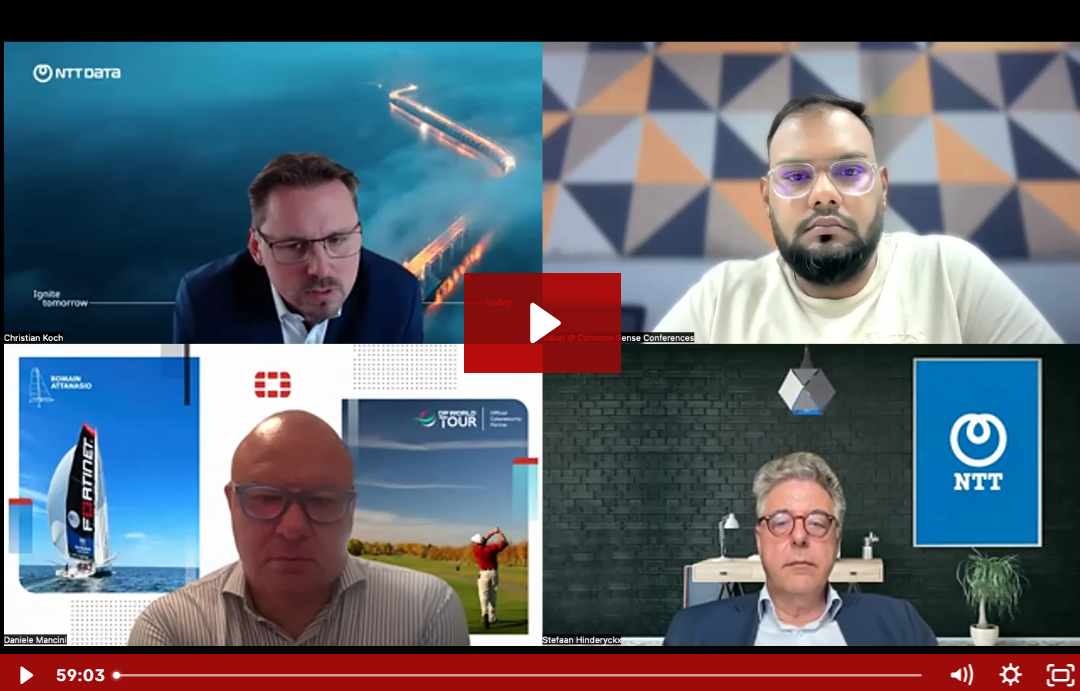
From Assumed Breach to AI-Driven Defense: Elevating OT Security
With phishing and ransomware threats rising dramatically, managing disparate security solutions and bridging IT-OT gaps has become a critical priority for enterprises striving to protect their cyber-physical systems. Watch the recording of the Fireside Chat where Industry experts Fortinet and NTT DATA experts, Daniele Mancini, Stefaan Hinderyckx, Christian Koch discussed proven strategies for building secure-by-design
Cybersecurity at the crossroads
Is your organization prepared for the future of cybersecurity? At a time when threats are evolving faster than ever, many companies face a dilemma: how do you keep innovating without sacrificing security? This Fastly whitepaper delves into the real challenges facing security teams and explains why tool consolidation, automation and a culture of “security by
WAF Buyer’s Guide
Are you ready to modernize the protection of your web applications and APIs? In an environment where threats are constantly evolving, having an effective web application firewall (WAF) is no longer optional – it’s essential. Fastly’s WAF Buyer’s Guide will help you identify which solution best suits your current needs and will allow you to
Reasons Why Your Company Needs a Password Manager
🔐 Security starts with trust — and a strong password manager.In a world where efficiency, data privacy, and controlled access are critical, NordPass offers the ideal solution for modern businesses. From IT to HR, from Sales to Marketing: sensitive data stays protected and accessible at all times. 📥 Download the whitepaper now to discover how
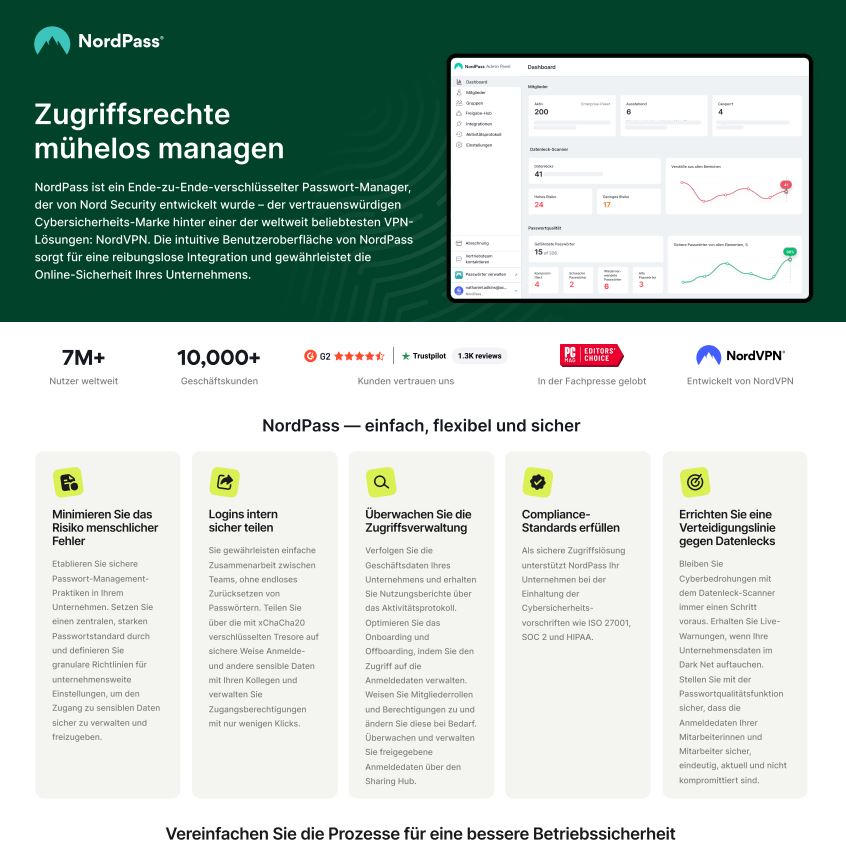
Effortlessly Manage Access Rights
NordPass is an end-to-end encrypted password manager developed by Nord Security, the trusted cybersecurity brand behind one of the world’s most popular VPN solutions: NordVPN. NordPass’s intuitive user interface ensures seamless integration and safeguards your company’s online security. Would you like it adapted for marketing purposes or kept strictly formal?
Mitigazione proattiva dei ransomware
Scopri la guida Proactive Ransomware Mitigation di Recorded Future, una risorsa essenziale per aiutare le organizzazioni a proteggersi in modo efficace dagli attacchi ransomware. Questo documento offre strategie e best practice per anticipare, rilevare e rispondere alle minacce. Punti chiave trattati: Comprendere il funzionamento del ransomware Identificare le vulnerabilità sfruttate dagli attaccanti Applicare una strategia
Guida all’acquisto della threat intelligence
Scopri la Guida all’Acquisto dell’Intelligence sulle Minacce di Recorded Future, un documento progettato per aiutare le organizzazioni a selezionare la migliore soluzione di intelligence sulle minacce in base alle loro esigenze specifiche. La guida fornisce criteri e raccomandazioni chiave per ottimizzare la strategia di cybersecurity. Punti chiave trattati: Definizione e importanza dell’intelligence sulle minacce Criteri
6 informazioni chiave dal rapporto sullo stato dell’intelligence delle minacce per il 2024
Scopri l’infografica di Recorded Future, che riassume le principali conclusioni di un sondaggio condotto su oltre 550 dirigenti, manager e professionisti della cybersecurity. Il documento offre una panoramica delle tendenze attuali e delle prospettive future dell’intelligence sulle minacce. Punti chiave trattati: Uso strategico dell’intelligence sulle minacce Aumento degli investimenti Maturità dei programmi Giustificazione degli investimenti
The Economics of Penetration Testing for Web Application Security
Web Application Security is a big challenge for developers und cybersecurity experts confronted with the fast pace of DevOps code changes. Penetration tests are among the many tools used for security, which is an authorized simulated cyberattack from a hacker’s perspective. “Pen tests” provide a deep dive look into a web app’s state of security,
Keeping your External Attack Surface Under Control
You can’t stop the expansion of your external attack surface, but you can identify unknown assets and their vulnerabilities to mitigate the security risk. External attack surfaces expand due to modern software development practices, mergers and acquisitions, the adoption of multi-cloud strategies and much more. Many organizations find it difficult to monitor these changes and